Our Products
We build network security applications that are simple to operate and awesome at threat detection
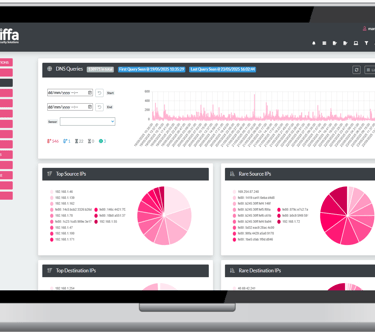
The Network Detect Manager
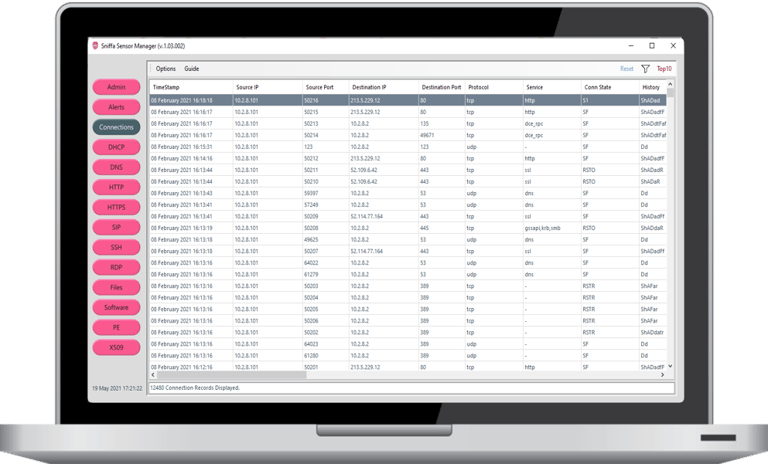
The Network Detect Sensor Manager Application will install onto any currently supported Microsoft Windows Operating System and is used to centrally manage multiple Sniffa Sensors deployed on your network. This application allows you to configure and deploy security rules to your IDS sensors, receive traffic logs and IDS alerts from remote sensors, dynamically analyse network meta-data, and display detected anomalies in a simple-to-use graphical user interface.
Overview
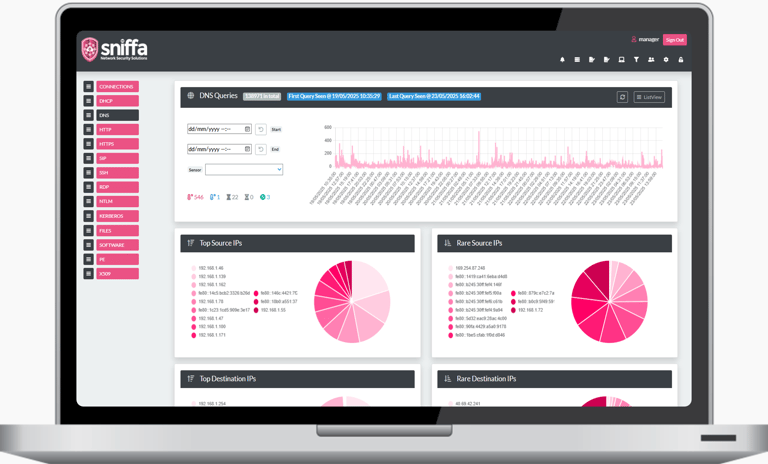
Once you have deployed your sensors and are sending logs and alerts to your Sensor Manager Application you can start to filter, search, correlate and run threat hunts across the hundreds and thousands of network meta-data fields and IDS alerts that have been generated by your sensors. Threat hunting is a great way to be able to spot malware that is operational on your networks but has not yet been detected by other security tools, such as firewalls, proxies, anti-virus or endpoint detection technology. The Sensor Manager Application can help you identify protocol-misuse, scanning, brute force, HTTP, HTTPS and DNS tunnelling, beaconing to/from command-and-control C2 servers, the early stages of ransomware and signs of data exfiltration, to name but a few.
With the right-click of a mouse, any network event displayed in the Sensor Manager Application can be correlated with the exact packet capture that was recorded at the time the event was created and transferred from the sensor to the PC for analysis. Complex Wireshark filters can be generated on the fly to enable quick searches across all captured streams and pinpoint the specific packets relating to a suspected attack.
At any point in time, you can create and download informative snapshot reports (xls, pdf & doc) showing the network connections, protocols and anomalies discovered by the Sensor Manager Application and share them across your security operations teams.
The network meta-data that is collected will be stored in a Microsoft SQL Database which can be administered in-house and easily integrated with your other software running alongside with the Sensor Manager Application, enabling a more enhanced and collaborative threat detection capability. Having your data stored in Microsoft SQL Databases makes the task of back-up and restoring your data simpler for your colleagues and your databases can easily be shared across several Sensor Manager Applications for offline investigations by your security operations teams.
Included in a subscription purchase
Network Detect Sensor Manager Application Installer Package for Microsoft Windows.
Microsoft SQL Express LocalDB Database (included in the installer package).
Database Build Script for installing the Sensor Manager Database on a remote Microsoft SQL Server (if required).
Licence Activation Key to unlock the software for the duration of your subscription period and restricted to the purchasing options chosen.
Build Script and/or ISO Image for Sniffa Sensors (compatible for certain versions of Ubuntu platforms), provided with your Activation Key.
Sensor Manager Application Upgrades if they are released during your subscription period.
ASP.NET Web User Portal Application with RBAC, to be installed on a Microsoft IIS Server.
Splunk Application Pack for Threat Hunting Sniffa, Snort, Suricata and Zeek Metadata logs in Splunk Enterprise or Cloud.
Email support for the duration of your subscription period.
The Sensor Manager Subscriptions will be locked to a single server or PC seat using a subscription licence key, so running multiple management server seats will require multiple licence keys to operate. Contact us to discuss the best options for your networks.
MS Windows App
Web Portal
The Network Detect S2 Sensor
When you buy a subscription to the Network Detect Sensor Manager Application we will provide you with an .iso image to build Sniffa Sensors onto your own hardware or virtual appliance. You will provide the hardware. However, if you want to get started without that hassle, then you should purchase a S2 Open-Sensor and Sensor Manager Application Subscription together (bundle product).
Overview
After purchese, the Sniffa S2 Open-Sensor appliances will be installed with an unmodified version of the Ubuntu Server Operating System (latest 24.04 LTS) and installed with unmodified best-of-breed open-source threat detection software on your behalf (free of charge). The Sensors will be expertly pre-configured and designed to operate with our Sensor Manager Applications out of the box.
The term 'Open-Sensor' means exactly what it says on the tin, it is 'open'. That means you are able to install supplementary software alongside the pre-installed Threat Detection software that you might consider appropriate in your environments. As well as reducing your overall operating expenditure (OPEX), having an Open-Sensor approach, means our sensors will easily fit into any software upgrade or vulnerability patching lifecycles you already run within your network environments. What's more, you own the tin, so Open-Sensors can be re-formatted after your subscription expires and you can re-deploy to other projects as you require.


Appliance
The Network Log Hunter

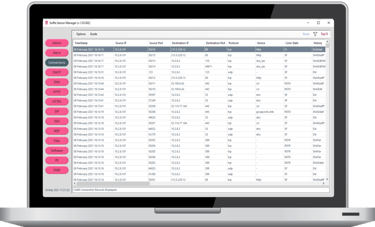
The Network Log Hunter Application is designed for the purpose of Threat Hunting logs generated by Zeek sensors and is compatible with all currently supported Microsoft Windows operating systems. With easy installation and user-friendly interface, the Network Log Hunter Application provides a method to granularly assess and analyse network activity, making it a valuable tool for network security analysts and engineers.
Overview
The Network Log Hunter can ingest Zeek logs either by locally importing Zeek .log files or remotely from Zeek Sensors over the network using the Syslog protocol. Using the simple to operate interface, you can filter, search, correlate and run threat hunts across the hundreds and thousands of network meta-data fields that have been generated by your sensors. Threat hunting is a great way to be able to spot malware that is operational on your networks but has not yet been detected by other security tools, such as firewalls, proxies, anti-virus or endpoint detection technology. The Network Log Hunter Application can help you identify protocol-misuse, scanning, brute force, HTTP, HTTPS and DNS tunnelling, beaconing to/from command-and-control C2 servers, the early stages of ransomware and signs of data exfiltration, to name but a few.
The network meta-data that is collected will be stored in a Local or Remote Microsoft SQL Database, of which the local version is included in the installer package. Having your data stored in Microsoft SQL Databases makes the task of back-up and restoring your data simpler for your colleagues and your databases can easily be shared across several Network Log Hunter Applications for offline investigations by your security operations teams.
Included in a subscription purchase
Network Log Hunter Application Installer Package for Microsoft Windows.
Microsoft SQL Express LocalDB Database (included in the installer package).
Database Build Script for installing the Network Log Hunter Database on a remote Microsoft SQL Server (if required).
Licence Activation Key to unlock the software for the duration of your subscription period and restricted to the purchasing options chosen.
Network Log Hunter Application Upgrades if they are released during your subscription period.
Email support for the duration of your subscription period.
Network Log Hunter Subscriptions will be locked to a single server or PC seat using a subscription licence key, so running multiple PC seats will require multiple licence keys to operate. Contact us to discuss the best options for your networks.
MS Windows App
The Network Log Viewer


The Network Log Viewer Application is compatible with all currently supported Microsoft Windows operating systems and is designed for the purpose of viewing Zeek logs created by Zeek sensors. This entry-level application is offered to our customers FREE of charge, as a means of demonstrating the benefits of the open-source Zeek network monitoring tool. With easy installation and user-friendly interface, the Network Log Viewer Application provides a convenient way to assess and analyse network activity, making it a valuable tool for network administrators and security professionals.
Overview
The Network Log Viewer Application is a tool used for importing Zeek .log Files into a local database, allowing you to easily sort, filter, and view network metadata from a Microsoft Windows desktop. With this application, you can filter the network log tables to find top and rare elements of individual protocols, and each view can be exported in .csv format for offline sharing. To get your hands on a FREE copy of the Network Log Viewer Application, contact us to find out where to download it.
MS Windows App
Available to buy Online
Click 'Buy Online' from one of the options below and you will be connected to our payment platform to complete your purchase.

1 Year Single Sensor Subscription Licence for the Network Log Hunter Application to be installed on any Microsoft Window OS
Bring Your Own Sensor Model
(we can provide free install images)


Sensor & Manager Bundle
1 Year Single Sensor Subscription Licence for the Network Detect Sensor Manager Application to be installed on any Microsoft Window OS
Bring Your Own Sensor Model
(we can provide free install images)
Network Detect Manager
1 Year Single Sensor Subscription Licence for the Network Detect Sensor Manager Application to be installed on any Microsoft Window OS and a Sniffa S2 Open-Sensor 1Gbps Appliance Pre-installed ready to go
If you cannot see the item that you would like to buy or you have additional questions regarding the purchase options, please contact us to discuss any requirements you might have.
We will be more than happy to help.
£1,125.00
£1850.00
£2,250.00
Network Log Hunter


Product Feature Matrix
Contact us
Whether you have a request, a query, or want to see a demo of our products, use the form below to get in touch with our team.